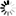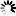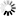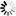Firewall Policies are groups of Firewall Services. Each policy constitutes a firewall definition that, when enabled on a connection, can provide customized access control between a Corente Services Gateway and its LAN, its partners, and the Internet. Each Corente Services Gateway User Group and tube associated with a particular Location can be assigned a unique Firewall Policy, to prevent specific users, on either end of the connection, from using certain applications and protocols across the connection.
To view the Firewall Policies currently defined in your domain, do the following:
Open the Firewall Policies branch in the domain directory.
Select Firewall Policies in the domain directory and view the table on the right side of the interface. This table displays the following:
Firewall Policy: The name of the policy.
Out Default: The default behavior for outbound Firewall Services that are not specified (Deny, Allow, or Continue to the next policy).
Exceptions: The number of specified Firewall Services for outbound traffic.
In Default: The default behavior for inbound Firewall Services that are not specified (Deny, Allow, or Continue to the next policy).
Exceptions: The number of specified Firewall Services for inbound traffic.
Permission: The Locations that have permission to use this particular Firewall Policy (All, None, or Specified).
In Use: Whether or not the Firewall Policy is currently in use for any Location.
To view the definition of an existing Firewall Policy, open the Firewall Policy's branch in the domain directory. Three categories are displayed: Inbound, Outbound, and Policy Use.
Open the Inbound or Outbound branches to see what Firewall Services have been specified for that direction. A note in parenthesis for each of these branches will tell you whether the specified Firewall Services are allowed through the firewall but all other protocols/ports are denied (Allow Specified/Deny) or whether the specified Firewall Services are denied through the firewall but all other protocols/ports are allowed (Deny Specified/Allow).
Open the Policy Use branch to see what Locations are allowed to use the Firewall Policy in their personalities.
Selecting a Firewall Policy will display a graphical representation of the Firewall Policy on the right side of the interface that enables you to quickly view or edit that policy.
You can also use the Edit or Delete buttons in the App Net Manager toolbar to modify any existing Firewall Policy. Changes made to a Firewall Policy will change the personality configuration of any Locations using that particular service. If you delete a Firewall Policy currently in use by any of your Locations, the Locations will no longer be able to use this policy and will revert to the default policy for the corresponding type of connection.
Default Firewall Policies
Several predefined Default Policies are available in App Net Manager. The names of each of these Default Policies describe a connection that is possible to configure between Locations or Locations and Remote Users. These policies have been preconfigured, but can be modified and apply by default to all of the connections in your domain that correspond with their name. App Net Manager also enables you to define additional policies that can be used instead, such as those to be used for specific Locations.
When you create a tube, by default, the applicable Firewall Policy will be enabled on that tube. You can replace this Default Firewall Policy with another Default or Custom Policy, if you want to.
DMZ to Internet: This Firewall Policy is the default for how the Internet and your DMZ (if applicable) are allowed to contact each other via the Corente Services Gateway.
LAN to Client: This Firewall Policy is the default for all remote users-to-Location tunnels and describes how remote users are allowed to access the Location's LAN.
LAN to DMZ: This Firewall Policy is the default for how the LAN and your DMZ (if applicable) are allowed to contact each other via the Corente Services Gateway.
LAN to Extranet LAN: This Firewall Policy is the default for all Location-to-Location tunnels between a Location in your domain and a Location within the domain of an Extranet partner.
LAN to Internet: This Firewall Policy is the default for how each LAN is allowed to contact the Internet through its local Location gateway.
LAN to Location: This Firewall Policy is the default for how each LAN is allowed to contact its local Corente Services Gateway.
LAN to Remote LAN: This Firewall Policy is the default for all Location-to-Location tunnels inside your domain.
Add a New Firewall Policy
To define a Firewall Policy, do the following:
If defining an existing Default Policy, select that policy and click the Edit button in the App Net Manager toolbar.
If defining a new Custom Policy, make sure Firewall Policies is selected in the domain directory and do the following:
Select the New button in the toolbar.
From the File menu, select Add Firewall Policy.
Right-click Firewall Policies in the domain directory and select Add Firewall Policy.
The Add Firewall Policy window is displayed.
Because these firewalls are stateful and a pseudo connection state is created for connectionless protocols like ICMP, you need only configure a Firewall Policy for connection initiation and not for return traffic. In addition, this service includes a fixup module for active FTP so that Firewall Policies will automatically permit the appropriate return connection for FTP.
Complete each of the following fields and options:
Firewall Policy Name: If this is not a Default Firewall Policy, enter a name for your new Firewall Policy. This name may contain up to 30 alphanumeric characters. Underscores are allowed, but do not use tabs, spaces, or punctuation marks when creating this name.
Outbound Firewall Policy: The settings in this section affect all outbound connections in the tube on which this Firewall Policy is applied.
Allow/Deny Selected Firewall Services: Before selecting Firewall Services for the outbound definition of this policy, choose either Deny or Allow from the pull-down menu. Note that it is generally more secure to select the Allow option and ban all services but the few that you specify, rather than to select the Deny option and allow all services over the connection besides the few that you specify.
When Deny is selected, choose Firewall Services from the Selected Firewall Services list to indicate the traffic that you would like to restrict from passing outbound through the firewall. All other outbound traffic will not be denied by this policy. You must then choose how to handle this non-denied traffic, using the Allow/Continue if no match on selected Services option.
When Allow is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly denied, the outbound traffic will be allowed to continue to its destination through this tube.
When Continue is selected and this Firewall Policy is applied to a tube, if the traffic is not denied by the tube definition, the traffic will be forced to continue and try the next tube to see if it is allowed or denied by that definition. This option should not be selected in the Firewall Policy of the last tube in a partner connection, to ensure that the traffic that you do not want to block will reach its appropriate destination.
When Allow is selected, choose Firewall Services from the list to allow outbound through the firewall. You must then choose how to handle traffic that is not allowed by the firewall, using the Deny/Continue if no match on selected Services option.
When Deny is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly allowed in the tube definition, the outbound traffic will be blocked by the tube or rerouted to the Internet, if backhaul is enabled.
When Continue is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly allowed outbound by the tube definition, the traffic is allowed to continue and try the next tube to see if it is allowed or denied by that definition. This option should not be selected in the Firewall Policy of the last tube in a partner connection, to ensure that the appropriate traffic is blocked from reaching its destination and breaching the security of the firewall.
Selected Firewall Services: All Firewall Services, including both default services and custom services, that are defined in your domain's Firewall Services list will be available for selection in this list.
Inbound Firewall Policy: The settings in this section affect all inbound connections in the tube on which this Firewall Policy is applied.
Deny/Allow Selected Services: Before selecting Firewall Services for the inbound definition of this policy, choose either Deny or Allow from the pulldown menu. Note that it is generally more secure to select the Allow option and ban all services but the few that you specify, rather than to select the Deny option and allow all services over the connection besides the few that you specify.
When Deny is selected, choose Firewall Services from the list to indicate the traffic that you would like to restrict from entering inbound through the firewall. All other inbound traffic will not be denied by the firewall. You must then choose how to handle this non-denied traffic, using the Allow/Continue if no match on selected Services option.
When Allow is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly denied, the inbound traffic will be allowed to continue to its destination through this tube.
When Continue is selected and this Firewall Policy is applied to a tube, if the traffic is not denied by the tube definition, the traffic will be forced to continue and try the next tube to see if it is allowed or denied by that definition. This option should not be selected in the Firewall Policy of the last tube in a partner connection, to ensure that the traffic that you do not want to block will reach its appropriate destination.
When Allow is selected, choose Firewall Services from the list to allow inbound through the firewall. You must then choose how to handle traffic that is not allowed by the firewall, using the Deny/Continue if no match on selected Services option.
When Deny is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly allowed by the tube definition, the inbound traffic will be blocked by the tube, or rerouted to the Internet, if backhaul is enabled.
When Continue is selected and this Firewall Policy is applied to a tube, if the traffic is not explicitly allowed inbound by the tube definition, the traffic is allowed to continue and try the next tube to see if it is allowed or denied by that definition. This option should not be selected in the Firewall Policy of the last tube in a partner connection, to ensure that the appropriate traffic is blocked from reaching its destination and breaching the security of the firewall.
Selected Firewall Services: All Firewall Services, including both default services and custom services, that are defined in your domain's Firewall Services list will be available for selection in this list.
Firewall Policy Use
When you create a Custom Firewall Policy, you can specify which Locations in your application network will be allowed to enable this policy on their User Groups or tubes. Default Policies are available for use by all Locations.
To configure the use of a Custom Policy, click the Configure button. The Edit Firewall Policy Use Permissions window will be displayed.
Complete this screen as follows:
Allow all Locations to use Firewall Policy: Select this option to make this Firewall Policy available to all Locations in your domain.
Allow only Selected Locations to use Firewall Policy: To restrict the Locations in your domain that can enable this Firewall Policy on their connections, select this option. The names of all Locations within the domain will be displayed in the Selected Locations list. To allow a Location to use the Firewall Policy, select the checkbox next to the Location's name. Select as many Locations that should use this policy.
Click the OK button to store your changes or the Cancel button to close the window and discard your changes.
When you have completed configuration of this new Firewall Policy, click the OK button to store your changes or Cancel to close the window and discard your changes.
You must save your changes in order for your addition to take effect.
Firewall Policy Interface
When you select a Firewall Policy in the domain tree or the Firewall Policy table, a graphical representation of the Firewall Policy will be displayed on the right side of the interface.
All of the Firewall Services that have been defined in your domain will be listed in a column in the middle of the screen. On either side of this column are brick walls, representing the firewall both outbound and inbound.
The first wall, on the left, represents the outbound side of the firewall. The following table describes the icons on the outbound side.
Table 1 Guide to Outbound Firewall Icons
Icon | Meaning |
|---|---|
 | By default, all unspecified Firewall Services are denied outbound, and this particular Firewall Service is denied outbound. |
 | By default, all unspecified Firewall Services are denied outbound, but this particular Firewall Service is allowed outbound. |
 | By default, all unspecified Firewall Services are allowed outbound, and this particular Firewall Service is allowed outbound. |
 | By default, all unspecified Firewall Services are allowed outbound, but this particular Firewall Service is denied outbound. |
The second wall, on the right, represents the inbound side of the firewall. The following table describes the icons on the inbound side.
Table 2 Guide to Inbound Firewall Icons
Icon | Meaning |
|---|---|
 | By default, all unspecified Firewall Services are denied inbound, and this particular Firewall Service is denied inbound. |
 | By default, all unspecified Firewall Services are denied inbound, but this particular Firewall Service is allowed inbound. |
 | By default, all unspecified Firewall Services are allowed inbound, and this particular Firewall Service is allowed inbound. |
 | By default, all unspecified Firewall Services are allowed inbound, but this particular Firewall Service is denied inbound. |
You can quickly modify a Firewall Policy on this interface by right-clicking on either the outbound or the inbound walls beside a Firewall Service.
To allow a particular Firewall Service outbound (or inbound) when the firewall is denying that Firewall Service, place your cursor over the section of the wall representing the outbound (or inbound) side of the firewall beside that service.
Your cursor will change to
 , which indicates that you can choose to allow this
service. Right-click your mouse button and select Allow
Outbound (or Inbound) Traffic. A dialog box will appear to
confirm your action. Select OK.
, which indicates that you can choose to allow this
service. Right-click your mouse button and select Allow
Outbound (or Inbound) Traffic. A dialog box will appear to
confirm your action. Select OK.
To deny a particular Firewall Service outbound (or inbound) when the firewall is allowing that Firewall Service, place your cursor over the section of the wall representing the outbound (or inbound) side of the firewall beside that service.
Your cursor will change to
 , which indicates that you can choose to deny this
service. Right-click your mouse button and select Deny
Outbound (or Inbound) Traffic. A dialog box will appear to
confirm your action. Select OK.
, which indicates that you can choose to deny this
service. Right-click your mouse button and select Deny
Outbound (or Inbound) Traffic. A dialog box will appear to
confirm your action. Select OK.
After making your changes, remember to save them.